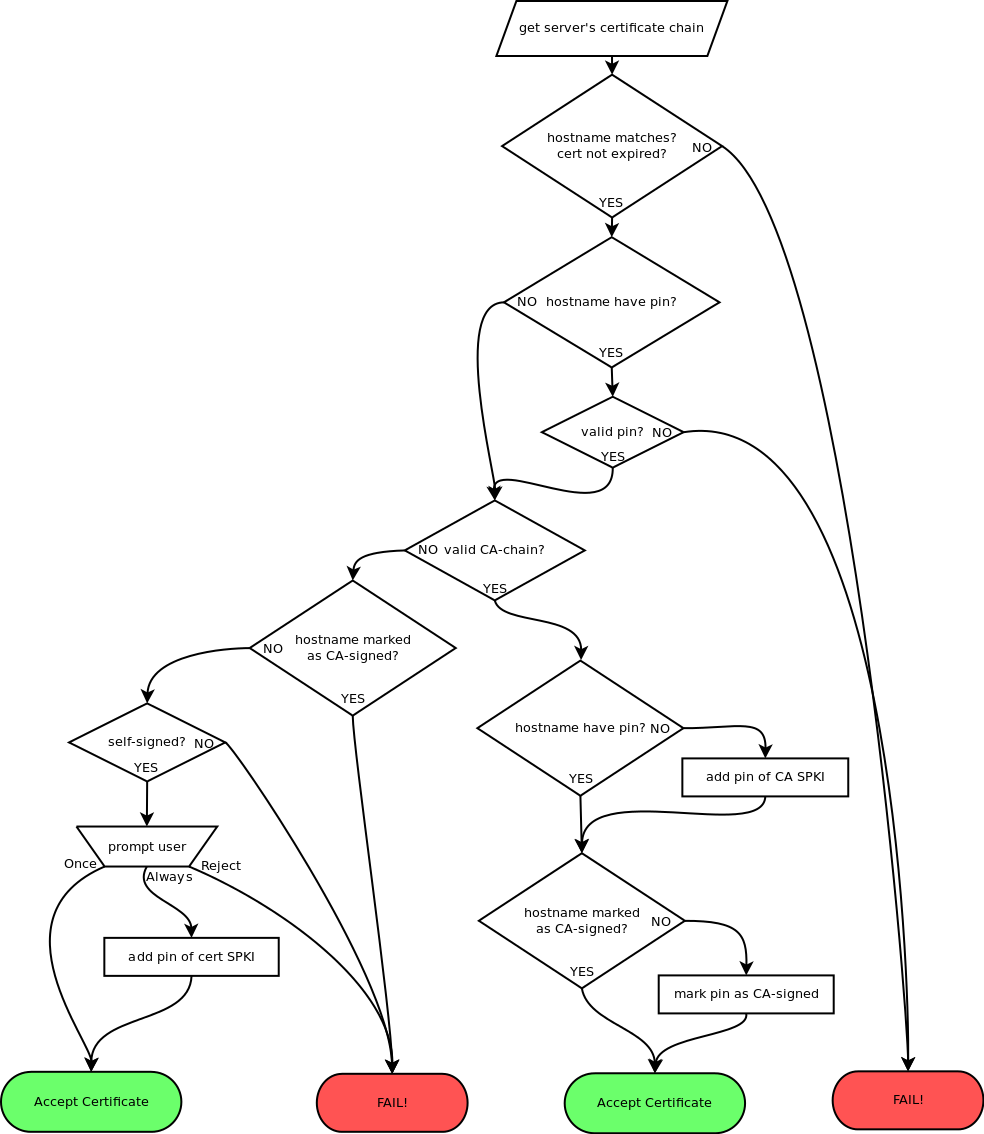
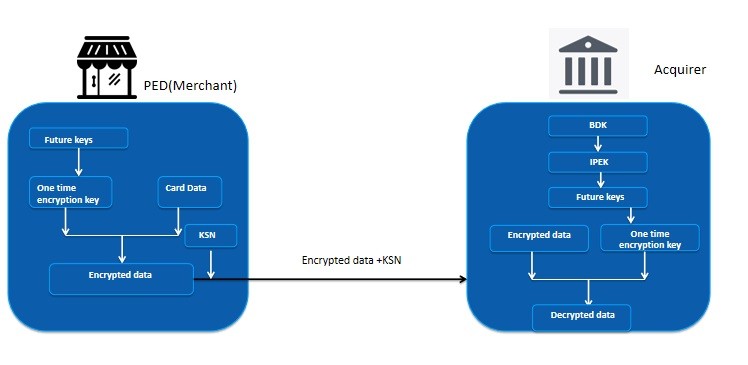
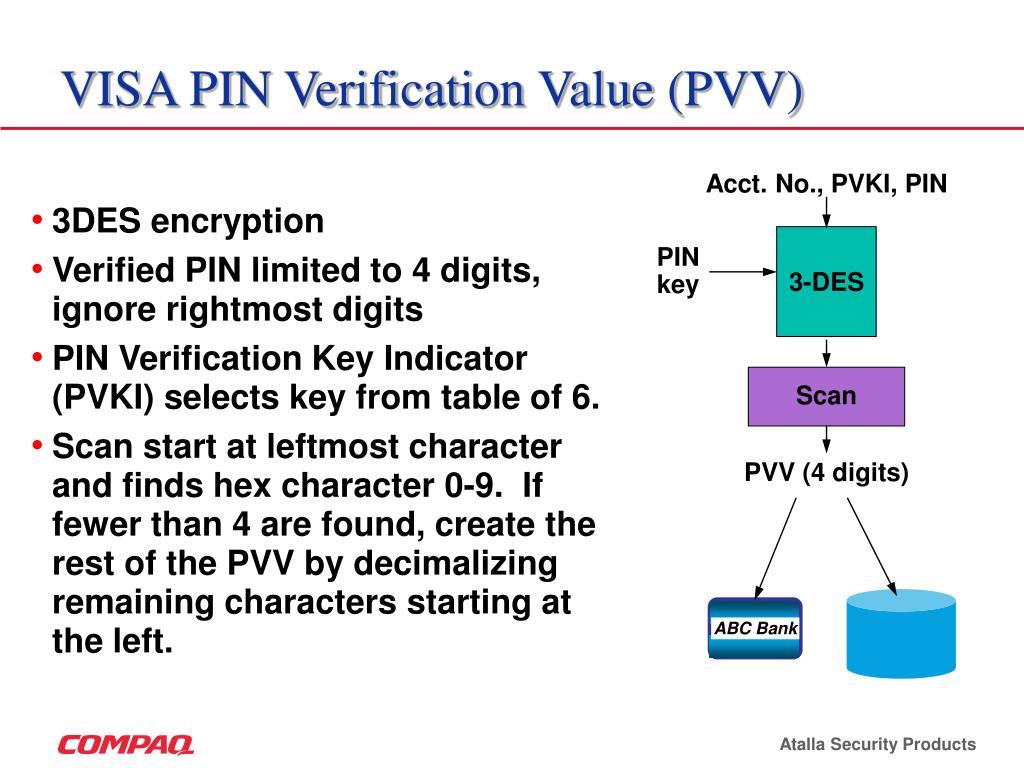
Decimalisation Table Attacks for PIN cracking “ It takes an average of 15 guesses to determine a four digit PIN using this technique, instead of the ppt download

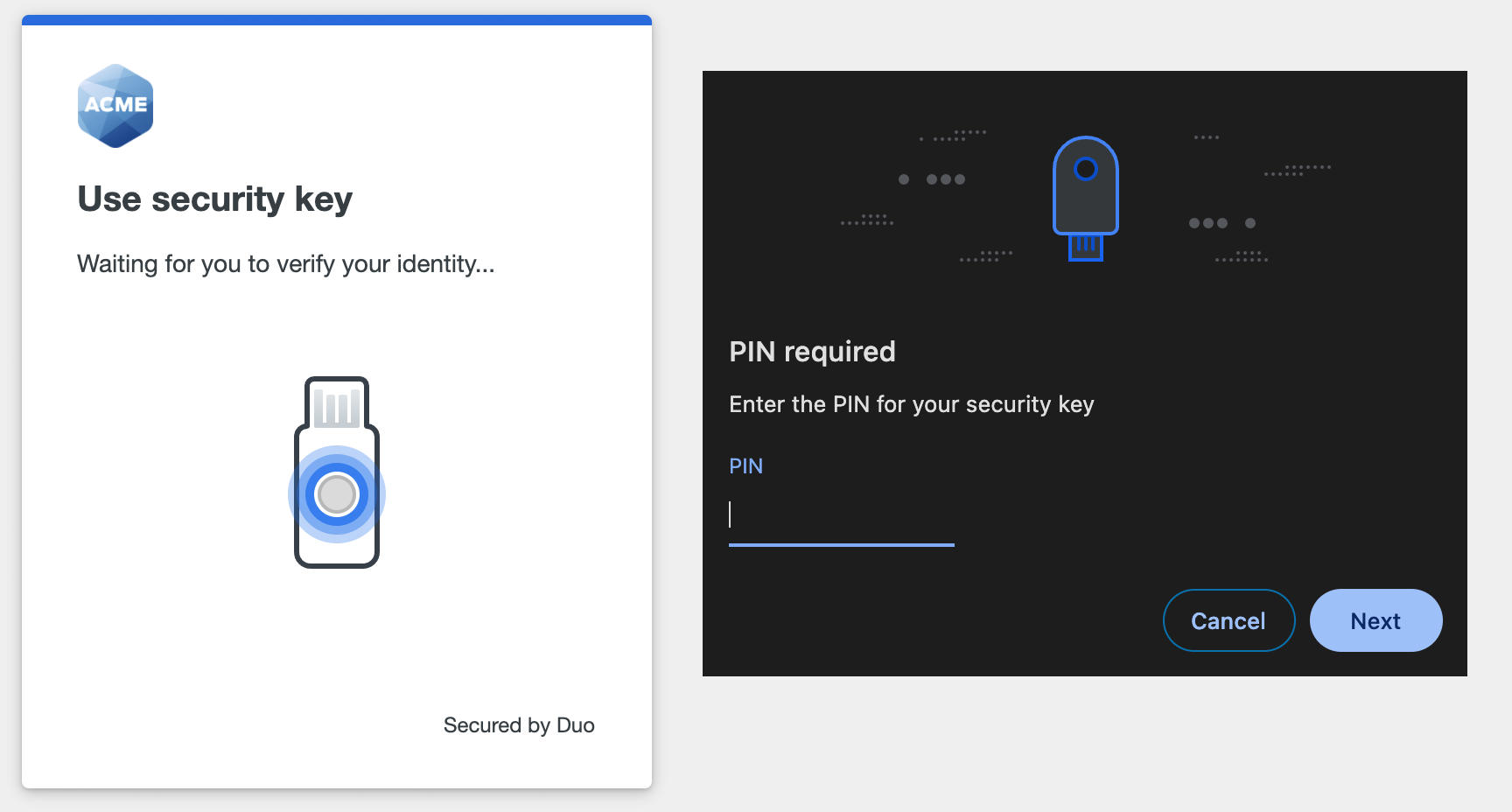
Follow-up on PIN verification against side-channel attack: KeepKey Hardware Wallet Under The Scope | Ledger

Pin Verification Stock Illustrations – 1,133 Pin Verification Stock Illustrations, Vectors & Clipart - Dreamstime









:max_bytes(150000):strip_icc()/personal-identification-number-FINAL-7c3eb9e610174683a6a99ba9f09b8fb6.png)